Back in 2007, the Burmese government reportedly severed the country’s Internet links in a crackdown over growing political unrest.
Yesterday, Burma once again fell off the Internet. Over the last several days, a rapidly escalating, large-scale DDoS has targeted Burma’s main Internet provider, the Ministry of Post and Telecommunication (MPT), disrupting most network traffic in and out of the country.
While motivation for the attack is unknown, Twitter and Blogs have been awash in speculation ranging from blaming the Burma / Myanmar government (preemptively disrupting Internet connectivity ahead of the November 7 general elections) to external attackers with still mysterious motives. The Myanmar Times reports the attack has been ongoing since October 25th (and adds the attack may impact Burma’s tourist industry).
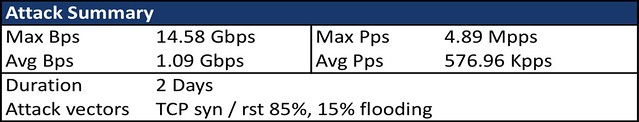
We estimate the Burma DDoS between 10-15 Gbps (several hundred times more than enough to overwhelm the country’s 45 Mbps T3 terrestrial and satellite links). The DDoS includes dozens of individual attack components (e.g. TCP syn, rst flood) against multiple IP addresses within MPT’s address blocks (203.81.64.0/19, 203.81.72.0/24, 203.81.81.0/24 and 203.81.82.0/24). The attack also appears fairly well-distributed — ATLAS data shows attack traffic across 20 or more providers with a broad range of source addresses.
A summary of the attack statistics in the chart below:
Most Burma Internet traffic goes through IPTel AS45419 (you can see a nice graph of the connectivity using HE’s ASInfo tool). And in turn, IPTel gets connectivity from Tata AS6453 (the majority of traffic), Beyond the Network AS3491 and NTT AS2914 amongst others. More information on MPT’s network is available on their home page (but this web site — and all of Burma for that matter — is currently unreachable).
Burma also lost Internet connectivity last Spring after the accidental severing of the trans-pacific SEA-ME- WE3 cable.
The DDoS (and possibly traffic engineering to mitigate the attack) generated hundreds of routing updates throughout the course of the day. Some sample BGP flaps from ATLAS routviews below:
11/02/10 03:50:16 Announce 203.81.81.0/24 XXXX 45419 45419 9988
11/02/10 03:53:25 Announce 203.81.81.0/24 XXXX 4766 4651 45419 45419 9988
11/02/10 03:53:51 Announce 203.81.81.0/24 XXXX 45419 45419 9988
11/02/10 04:04:56 Announce 203.81.81.0/24 XXXX 4766 4651 45419 45419 9988
11/02/10 04:04:56 Announce 203.81.81.0/24 XXXX 4766 4651 45419 45419 9988
11/02/10 04:05:24 Announce 203.81.81.0/24 XXXX 45419 45419 9988
11/02/10 04:05:24 Announce 203.81.81.0/24 XXXX 45419 45419 9988
11/02/10 04:08:32 Announce 203.81.81.0/24 XXXX 4766 4651 45419 45419 9988
11/02/10 04:08:58 Announce 203.81.81.0/24 XXXX 45419 45419 9988
11/02/10 04:11:42 Announce 203.81.81.0/24 XXXX 4766 4651 45419 45419 9988
11/02/10 04:12:09 Announce 203.81.81.0/24 XXXX 45419 45419 9988
11/02/10 04:12:09 Announce 203.81.81.0/24 XXXX 45419 45419 9988
11/02/10 04:17:30 Announce 203.81.81.0/24 XXXX 4766 4651 45419 45419 9988
11/02/10 04:17:30 Announce 203.81.81.0/24 XXXX 4766 4651 45419 45419 9988
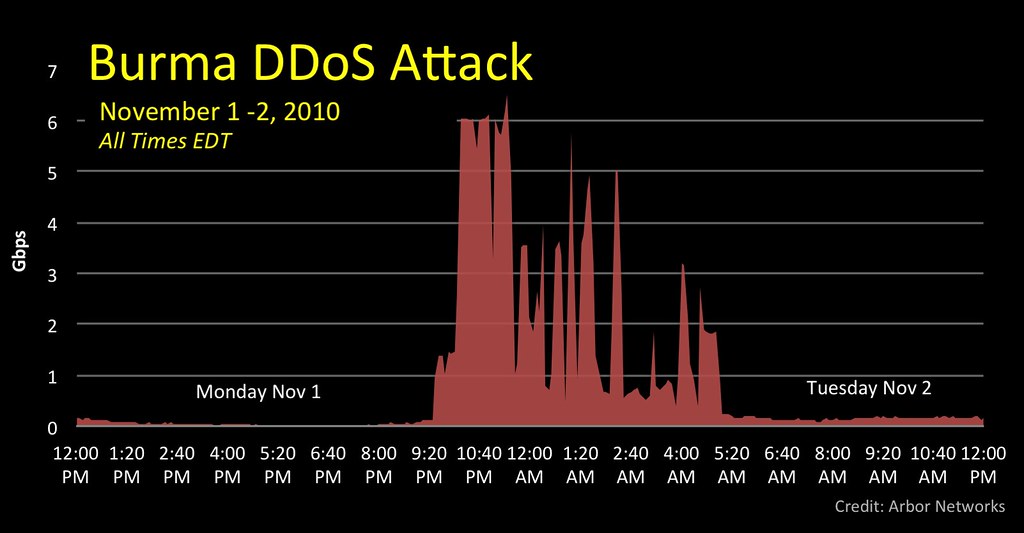
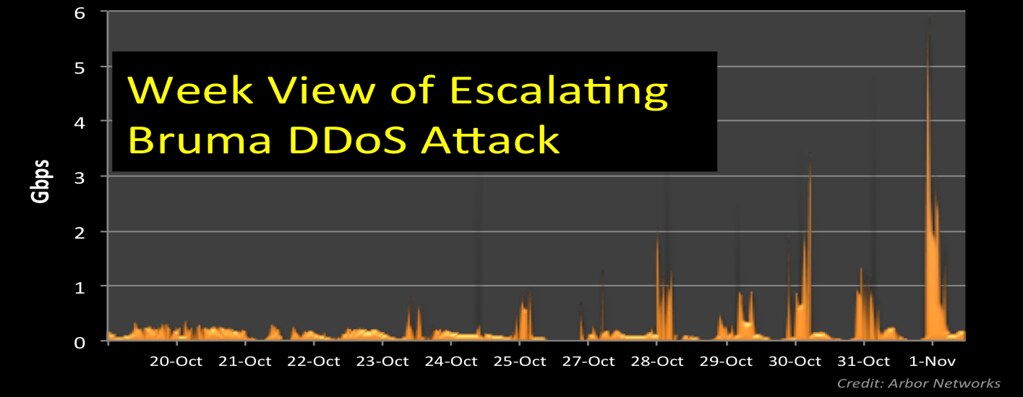
In the last two graphs, I show traffic to Burma (AS9988) through 80 randomly selected ATLAS ISPs. The top graph shows the last two days and the bottom providers a view of the past week. Normally Burma traffic peaks around 100 Mbps. Over the course of the week, the rapidly escalating attack jumped into a sustained multi-gigabits per second. All times are EST.
A quick look at anonymous ASPath traffic data suggests a number of upstreams have begun to blackhole traffic to MPT address space in response to the attack.
While DDoS against e-commerce and commercial sites are common (hundreds per day), large-scale geo-politically motivated attacks — especially ones targeting an entire country — remain rare with a few notable exceptions. At 10-15 Gbps, the Burma attack is also significantly larger than the 2007 Georgia (814 Mbps) and Estonia DDoS. Early this year, Burmese dissident web sites (hosted outside the country) also came under DDoS attacks.
At present I do not know the motives for this attack but our past DDoS analysis have observed the gamut from politically motivated DDoS, government censorship, extortion and stock manipulation. I’ll update this blog if I get more details.
Credit to Jose Nazario for assisting with some of this analysis.
What the fuck is this !!!
Really after this damage anybody can easily understand How cruel technology is ???