LilyGo T-Dongle S3. is a tiny USB device is like a Swiss Army knife for cybersecurity pros, red teamersu it’s small, cheap and powerful.

Where to start?
-Get a T-Dongle-S3 Here for less than $15

The Spec:
- – Microcontroller: ESP32-S3 (Dual-core Xtensa LX7, up to 240 MHz)
- – Memory:
- – 16MB Flash
- – 8MB PSRAM
- – 512KB SRAM
- – Wireless:
- – Wi-Fi 802.11 b/g/n (2.4 GHz)
- – Bluetooth 5.0 LE
- – Display: 0.96-inch OLED (SSD1306, 128×64 resolution, I2C)
- – USB: USB-A interface, supports USB 2.0 (via CH340 for serial communication)
- – Power:
- – 5V via USB
- – Optional battery support (with charging circuit, typically for 3.7V LiPo)
- – GPIO: Limited exposed pins (depends on model, often 6-8 usable GPIOs)
- – Sensors/Features:
- – Optional TF card slot (some variants)
- – RGB LED
- – Reset button
- – Dimensions: Approx. 30 x 20 x 10 mm (USB dongle size)
- – Programming: Supports Arduino, MicroPython, ESP-IDF
What USBArmyKnife Can do?
– USB Device Emulation: Mimics various USB devices, such as:
- – Keyboards (for keystroke injection)
- – Mice (simulate cursor movements/clicks)
- – Storage devices (emulate USB drives)
- – Network adapters (RNDIS for network attacks)
- – Serial devices (CDC for communication)
- – Penetration Testing:
- – Execute payloads for security testing (e.g., scripts via emulated HID devices)
- – Deliver malicious or test payloads (e.g., reverse shells)
- – Protocol Analysis: Sniff or manipulate USB traffic for debugging or learning.
- – Custom Payloads: Write and deploy custom scripts using Arduino, MicroPython, or ESP-IDF.
- – BadUSB Attacks: Simulate rogue USB devices to test system vulnerabilities.
- – Cross-Platform: Works on Windows, Linux, macOS targets when plugged in.
- – Hardware Features (with T-Dongle S3):
- – Use onboard OLED to display status or logs.
- – Leverage Wi-Fi/Bluetooth for remote control or data exfiltration.
- – Store payloads on TF card (if supported).
How to install USBArmyKnife on a LilyGo T-Dongle S3?
First thing first format the micro sd card you will use to FAT32. Use a 32 Gb, 64 Gb and above are not officially supported due to hardware and firmware limitations, though some users report success with specific 64GB cards formatted as FAT32. For reliable performance, stick to 32GB or smaller.
No matter what operating system you use download the following files:
- -boot_app0.bin: https://github.com/espressif/arduino-esp32/blob/3.2.0/tools/partitions/boot_app0.bin
- –: https://github.com/i-am-shodan/USBArmyKnife/releases/download/v1.0.2/LILYGO-T-Dongle-S3.Firmware.binaries.zip
Connect the LiLYGo T-Dongle S3 on your computer in boot mode: hold the back button while you insert it your USB port, then release it when it’s connected. The screen will on in dark grey color.
Go to https://esp.huhn.me. Only Chrome, Edge and Opera are supported. Press connect, the carefully select the files you just downloaded in that particular order, adjust the values as shown bellow:
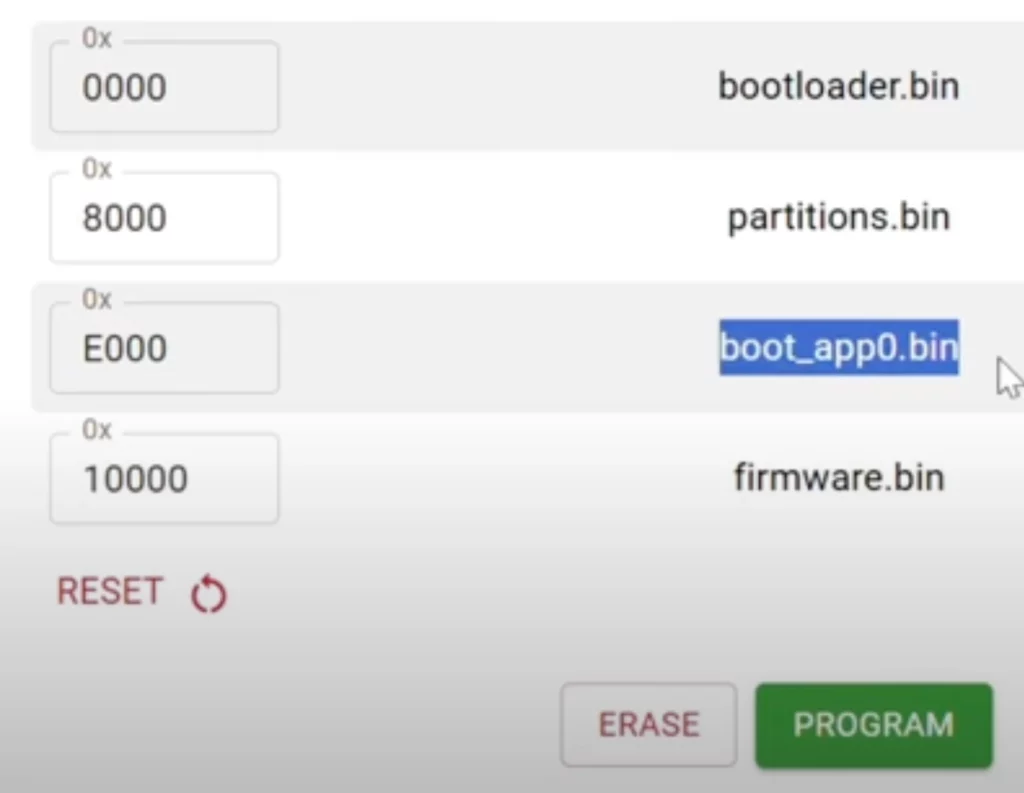
Press Program and the device will be flashed to install USBArmyKnife. Flashing will take a minute or 2. Disconnect the device once the process is finished, and reconnect it. Check on your mobile or computer the wifi network called “Iphone14”, default password is “password”, open your browser and go to http://4.3.2.1:8080 SSID and password can be changed in the preferences.
Et voila, have fun!
