A interesting paper on shellcode for PPC plateform, finally someting for the rest of us. Shellcode instructions are the actual assembly commands that can lead to give remote access to the attacker. The most common shellcode instruction is to execute a shell (such as /bin/sh). Other common shellcode routines will add a root user account to the system, or perform a reverse telnet back to the attacker?s machine.
The most common shellcode instruction is to execute a shell (such as /bin/sh). Other common shellcode routines will add a root user account to the system, or perform a reverse telnet back to the attacker?s machine.
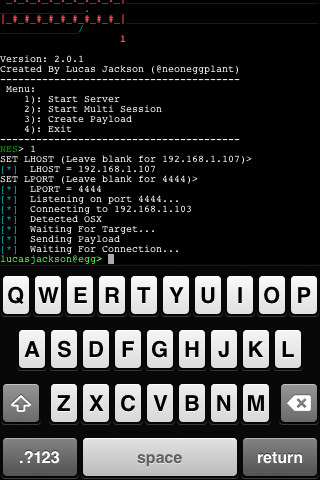
This paper covers the OSX (darwin) system calls, the PowerPc subroutines, several exemple of shellcode.
Don’t play with that if you don’t know what you do!
Grab your copy of [url=https://deepquest.code511.com/blog/images/uploads/txt/PPC_OSX_Shellcode_Assembly.pdf]PPC OSX Shellcode Assembly pdf format (284kb)[/url]
Armor2net Personal Firewall allows the user to grant and deny access to the Internet on a per-application basis, which will prevent harmful worm, Trojan horse, and spyware programs from infiltrating your computer. The program also alerts you of any intrusive behavior coming from the Internet.